The ability to own and to transfer assets via transactions is at the heart of economic value creation. And to keep track of these business agreements, market participants have always relied on ledgers. But to make sure that these ledgers remain accurate and are not being tampered with by fraudulent market participants, most business networks rely on central, trusted parties, such as banks or other intermediaries, to oversee these business ledgers and to validate each transaction that is taking place within the network.
This need for an intermediary has become even more important in the modern age, as assets have increasingly been digitalised and central third parties are required to make sure that a digital asset is not duplicated and spent more than once by the same party. But while the use of such a central intermediary brings the major benefit of introducing trust into the system, it also comes with certain limitations, such as the introduction of bottlenecks into the network, leading to a slowdown in transaction processing speed and an overall lack of transparency.
Blockchain technology offers a solution to these issues by introducing a shared, incorruptible ledger whose integrity can be ensured without the need for a central intermediary. A blockchain is a shared – or distributed – database capable of processing and recording all transactions taking place within a network on a peer-to-peer basis, eliminating the traditional need for a third party to record and verify single transactions, and creating an immutable transaction history.
Read More: Blockchain Technology – Overview, Features and Types
How the Blockchain Works?
1. The Blockchain Lifecycle
The blockchain’s name essentially describes the workings of the underlying technology. A blockchain consists of a chain of data blocks containing the entire history of transactions that have taken place among all members of the network since its initiation. The chain is continuously expanded by new blocks containing the data of recent transactions that have occurred within the network.
A single block can be compared to a page within a ledger, and its creation and connection to the existing chain of blocks always follow the same process. First, a transaction is created by a participant of the blockchain network. This transaction, as well as a cryptographically secured digital signature of the sender proving the transaction’s authenticity, is then broadcasted to the entire network of users (nodes). Subsequently, the nodes will verify the authenticity of this transaction by decrypting the digital signature of the sender, after which it is pooled together with other recent transactions into a block of data. This block of recent transactions is then again transmitted to the (validating) nodes in the network, which are now required to validate the block. This process requires the implementation of a specific consensus mechanism in the blockchain protocol. Once the block has been validated, it is added to the existing chain of blocks. With the chaining of subsequent blocks to this block, all the transactions contained within this block become a permanent part of the distributed ledger. Continuous updating of the entire chain enables each node within the network to validate, at any point in time, the status of the blockchain.

As one of the key aspects of a specific blockchain’s workings is the consensus mechanism it employs to verify transactions within its network. Various approaches to such a consensus mechanism have been developed, and the two most prominent protocols shall be presented in the following: the proof-of-work and the proof-of-stake mechanism.
2. Consensus Mechanisms
It is only after a formal approval that a transaction will be executed on a blockchain. But the absence of a traditional middleman to verify and approve transactions within a blockchain network requires the introduction of a new mechanism that allows for a reliable verification within an anonymous environment. As any node within a blockchain network can create a new block of transaction data, the network needs a mechanism that decides which block should eventually become part of the unique existing blockchain.
This role is taken up by a so-called consensus mechanism. In the absence of trust between transaction partners, such a mechanism is defined by certain parameters, as depicted in the following table, allowing it to replace the usually required middleman to clear transactions and ensure a reliable transaction environment.
| Parameter | Explanation |
| Decentralized governance | A single central authority cannot provide transaction finality. |
| Quorum structure | Nodes exchange messages in predefined ways, which may include stages or tiers. |
| Authentication | It provides means to verify the participants’ identities. |
| Integrity | It enforces the validation of the transaction integrity (e.g., mathematically through cryptography). |
| Nonrepudiation | It provides means to verify that the supposed sender has really sent the message. |
| Privacy | It helps ensure that only the intended recipient can read the message. |
| Fault tolerance | The network operates efficiently and quickly, even if some nodes or servers fail or are slow. |
| Performance | It considers throughput, liveness, scalability, and latency. |
Based on these parameters, many different consensus mechanisms have been developed over time. And while all of them work towards the same goal of ensuring a trustless and secure transaction environment by establishing a single version of the truth, each alternative features varying degrees of speed, cost, scalability, privacy and network security. In the following, the focus will be laid on two substantially different consensus protocols: Bitcoin’s proof-of-work protocol and the proof-of-stake protocol.
2.1.The Proof-of-Work Mechanism
The proof-of-work protocol, even though already having been developed in its essence in 1999, is one of the most widely used consensus mechanism today. Within the Bitcoin blockchain, this mechanism, also known as mining, serves two main purposes. First of all, it prevents network participants from tampering with the transaction data on the blockchain, thus allowing for trustless consensus among network participants and ensuring security, while secondly creating new Bitcoins.
A proof-of-work protocol requires network nodes, also known as miners, to run complex mathematical computations to validate the pool of recent transactions within the proposed block. This ensures that the validating nodes have invested significant resources in the form of processing power, bandwidth and electricity to verify transactions, a process for which they are compensated in return.
The mathematical computations performed by the nodes transform certain pieces of data into a unique and seemingly random sequence of letters and numbers known as a hash, as is depicted in the following figure. While it is easy to transform data into a hash by applying a certain hashing algorithm, it is practically impossible to backwards-translate a hash into the original data, and any minor change of inputs will furthermore result in an entirely different hash.

Within the proof-of-work-mechanism, a block hash is created by applying the SHA-256 algorithm to distinct pieces of data, among which are the hash of the previous block on the chain, a binary hashing of all the transactions pooled in the current block (also known as the Merkle Root), a timestamp of the hashing, and the nonce, a random number that is varied constantly.
Miners put these pieces of data through the hashing algorithm and compare the resulting hash with a certain arbitrary condition set by the network, also known as target. As hashes are one-way functions, it is practically impossible to find an acceptable hash value just by looking at the current target. Random guessing is the only possibility for a miner to hunt for a solution to the target, and thus large computing power is required to be able to compete for the discovery of a solution with other miners in the network.
Should the computed hash comply with the target, the miner has solved the mathematical problem, proof-of-work has been generated, the block is linked to the local copy of the blockchain, as is depicted in the following figure, and propagated to the entire network. For this, the successful miner is rewarded with Bitcoins, thus incentivizing the provision of computing power for the validation of transactions.
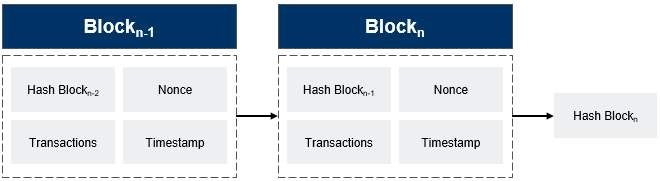
Three factors relating to this proof-of-work mechanism add to the security of the Bitcoin blockchain: First of all, it is not possible to predict which miner will find the solution to the target, consequently making it impossible to predict which block will be added to the blockchain at any point in time. Furthermore, the hash of each block on the blockchain includes the respective hash of its preceding block. As a hash value changes entirely when making even the slightest change to the input data, manipulating a certain transaction within a previous block on the blockchain would require the recalculation of the hash of that respective block and of those of all the consecutive blocks on the chain. Considering the effort needed to find the solution to a single block, such a manipulation becomes practically unfeasible. And third, potential double-spending by network participants is prohibited by the proof-of-work mechanism. When mining, nodes always built on the longest existing version of the blockchain. Thus, while a miner might be engaged in the manipulation of a historic block of the chain, the chain is continuously expanded by other miners. Thus, to force the network to accept the manipulated version of the blockchain, a miner would have to lengthen the chain quicker than the other nodes in the network were lengthening it originally. This would require the malevolent attacker to control more than 50 per cent of the computing power within the network – which should be practically impossible and/or completely uneconomical. As a consequence, the proof-of-work mechanism enables the network to achieve consensus in the absence of trust by making it prohibitively expensive to try to manipulate the blockchain.
The question that remains to be answered is how this mechanism leads to a unique chain that is characterized by consensus across the network. As the ability to generate blocks is a show of computational strength, which is just what the Bitcoin network needs to help verify all the transactions. But it is also a show of community spirit because by agreeing to enter the contest for the next block, they show themselves to be willing to respect the interests of the community rather than manipulate the block chain for self-interested purposes. Put otherwise, as it is assumed that most the network participants are honest, when in doubt, the longest blockchain will always be the ‘correct’ blockchain. This chain enjoys the consent of all nodes, as a manipulated blockchain will never be able to outpace the honest chain.
The proof-of-work mechanism suffers from certain limitations. Most importantly, as has been described earlier, a proof-of-work protocol requires the input of significant computational effort and, thus, resources to verify transactions. For instance, the annual power consumption required for the entire Bitcoin mining operations can be compared to Ireland’s average annual electricity consumption. Depending on the availability of respective mining hardware, mining can become an uneconomical venture for nodes, as electricity costs can outweigh the reward for mining and moreover raises ecological questions. Furthermore, the fact that the amount of computing power required to be able to sustain a profitable mining activity is prohibitively expensive for the average person favours the concentration of computing power on singular nodes. This, in turn, yields the danger of a 51 per cent attack and contradicts the blockchain’s idea of decentralisation.
Finally, a question that remains to be answered is what happens to a proof-of-work system once all units of its underlying cryptocurrency have been mined. Since miners only perform the work necessary to validate transactions out of the economic incentive of being rewarded for this work with Bitcoins, the finite supply of Bitcoins might lead to transaction validation activity breaking down once this supply runs out. While some authors predict that transaction fees will continue to provide sufficient incentive for mining activities to be upheld, it remains to be seen whether the cost of the validation activity will be sufficiently low in the future to be covered by the small transaction fees received by miners on the Bitcoin blockchain.
2.2.The Proof-of-Stake Mechanism
Due to the disadvantages of a proof-of-work mechanism (especially the environmental impact due to the high energy consumption), proof-of-stake was first proposed as an alternative consensus mechanism in 2012 and offers a completely different approach to the computing power-based proof-of-work mechanism. Within a proof-of-stake consensus mechanism, a node’s ability to add blocks to the blockchain is directly related to its respective ownership stake in the cryptocurrency. Thus, a node that possesses five times more coins than another node would be able to validate five times more blocks than the other. In other words, block validation is made easier for those nodes that own a larger stake in the network, the motivation behind this being to give more power to those network participants that have the strongest incentive to be good stewards of the system. Thus, in a sense, a proof-of-work mechanism seeks to guarantee validity by requiring a high input of work, while a proof-of-stake mechanism seeks to guarantee validity by requiring validators to invest in a stake as collateral.
The general process of block validation under a proof-of-stake mechanism can be described as follows. A certain number of currency holders decides to place their coins within a proof-of-stake mechanism and thus become validators. The algorithm then chooses one of these nodes to become the validator for the next block based on a weighting that is dependent on their respective deposit size. Thus, a node with ten coins will be ten times as likely to be chosen as validator than a node with one coin.
In addition to the proof-of-work and proof-of-stake protocols, a wide range of other consensus mechanisms has been developed. But as each consensus mechanism has its unique advantages and shortcomings, it is important to note that the choice of a consensus mechanism is very much dependent on the architecture and purpose of the blockchain in question.