An ethical hacker is a security professional who helps organization to take defensive measures against malicious attacks and usually the process he doing to find those vulnerable point is called Ethical Hacking. Sometimes this is also known as Penetration Testing or Intuition Testing. In this case, the ethical hackers are getting into the minds of computer criminals; think like them to find about innovative ways the hackers may use to get into the systems. Then organizations can take required actions to avoid those vulnerabilities. It has identified that the almost all computer systems have vulnerabilities that can be exploited by a hacker to come to do damages. This can be due to an unpatched application, a misconfigured router or a Continue reading
Business Information Systems
Social Engineering Attacks
The rise of 21st century marked the transition phase of the most global businesses towards a paperless office environment, where the focus shifted the manual to the computerized form of work culture. But at the same time, change brought a number of threats and menace in terms of one of the biggest issues of the current businesses, the social engineering used among the hackers for cracking techniques that rely more on human weaknesses rather than technology itself. The aim or motive of such attacks was getting access to passwords or other relevant information by tricking people for carrying out illegal or criminal activities. FBI and other security experts hold a firm view that majority of threats originate from the internal Continue reading
What is Expert System?
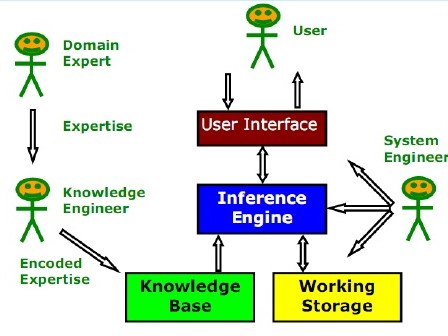
An expert system is an advanced computer application that is implemented for the purpose of providing solutions to complex problems, or to clarify uncertainties through the use of non-algorithmic programs where normally human expertise will be needed. Expert systems are most common in complex problem domain and are considered as widely used alternatives in searching for solutions that requires the existence of specific human expertise. The expert system is also able to justify its provided solutions based on the knowledge and data from past users. Normally expert systems are used in making business marketing strategic decisions, analyzing the performance of real time systems, configuring computers and perform many other functions which normally would require the existence of human expertise. The Continue reading
Case Study on Information Systems: Integrated Customer Ordering Service at Marks & Spencer
Marks and Spencer is one of the leading retail organizations in UK which sell stylish, quality and great value clothing and home products , also quality food. They are one of the most popular brand among people not only in UK but globally. They have more than 600 stores in UK and constantly increasing many more around the world. It was founded when in 1884, Michael Marks opened a stall at Leeds Kirkgate Market. In 1901, its first registered store was located at Derby street, Manchester. By 1924 they started expanding and the head office moved from Manchester to London. Implementation of new policies and maintenance of services and value kept on adding to the success of Marks and Spencer. Continue reading
What is Agile Methodology?
Engineering methodologies required a lot of documentation thereby causing the pace of development to slow down considerably. Agile Methodologies evolved in the 1990s to significantly eliminate this bureaucratic nature of engineering methodology. It was part of developer’s reaction against “heavyweight” methods, who desired to drift away from traditional structured, bureaucratic approaches to software development and move towards more flexible development styles. They were called the ‘Agile’ or ‘Light Weight’ methods and were defined in 1974 by Edmonds in a research paper. Agile methodology is an approach to project management, typically used in software development. It refers to a group of software development methodologies based on iterative development. Requirements and solutions evolve through cooperation between self-organizing cross-functional teams, without concern for Continue reading
Uses of Virtual Private Networks (VPN)
A Virtual Private Network (VPN) is a point to point connection that connects a user to a private network in a different location. Basically, VPNs are used to set up a secure connection to the internet. A VPN works by creating a point to point connection from a public wifi connection to a private wifi connection in a business or company building as if you are directly connected to the network. Since the normally accepted definition for a network is fairly common and usually accepted throughout the trade. A network consists of any variety of devices which may communicate through some arbitrary technique. Devices of this nature include computers, printers, and routers will reside in geographically numerous locations. The strategies Continue reading