It is necessary to understand some of the basics of encryption, digital certificates, and digital signatures before examining the components of a Public Key Infrastructure (PKI).
Encryption Overview
- “Encryption” is the term used to describe the process of taking legible data, and scrambling it into a form that is non-intelligible to anyone who doesn’t know how to unscramble (or “decrypt”) it again.
- Encryption processes usually involve a method for encrypting the data and one or more “keys”. The keys are usually a very long number and are used during the encryption or decryption process.
- In most cases, the method (or “algorithm”) that is used by an application to encrypt data is common knowledge and the key that is used is kept private.
- There are two main types of encryption – “symmetric encryption” (the same encryption key is used for encryption and decryption), and “asymmetric encryption” (different keys are used for encryption and decryption).
- Asymmetric encryption algorithms use two keys – a “public key” and a “private key”. The algorithm usually involves a mathematical step that is very easy to do one way, but very difficult to do in reverse.
Distinct Features of Algorithm
The algorithm is designed such that:
- Anything that is encrypted using the public key can be decrypted with the private key.
- Anything that is encrypted with the private key can be decrypted with the public key.
- The keys are generated in such a way that it is not possible to determine one key if you know the other.
This method of encrypting data using a widely publicized public key and a separate private key is also called “Public Key Cryptography” and is the type of encryption that is utilized by digital certificates.
Digital Certificates
A meaning for “certificate” is “A document testifying to the truth of something”. A digital certificate is an electronic “certificate” that contains information about a user and is used (among other things) to verify who the user is. Digital certificates make use of Public Key Cryptography. The public key is stored as part of the digital certificate. The private key is kept on the user’s computer, or in some hardware such as smart cards, i-keys, etc.
Digital certificates are based on the IETF X.509 series of documents.
The main uses of digital certificates are:
- Proving the identity of the sender of a transaction, non-repudiation, and checking the integrity of transmitted data (via the use of digital signatures).
- Encryption
- Single sign-on (the digital certificate can be used as an authorization key to connect to computer systems.)
If digital certificates are to be used for security and identification purposes, all of the following conditions must be met:
- Every certificate is unique.
- The owner of a certificate has been fully identified. All digital certificates are signed by the Certificate Authority (CA) that issues it. In issuing a certificate, the CA is basically saying that they have identified the user, and the user really is who they claim to be. To be able to trust a digital certificate, the CA needs to have fully identified the customer before issuing the certificate (or be satisfied that some other entity has adequately performed such identification).
- A private key can only be used by the owner of the certificate. As with all authentication schemes, the onus is on the user to keep the private key private. Usually, a password, a smart card, or biometric device is used to lock the private key and prevent others from using it.
Digital Signatures
A digital signature is used to verify the integrity of a block of data. Digital signatures are also used to verify the identity of the person who sent the transmission.
A digital signature is created as follows:
- A “digest” of the data is created. The digest is a short length of binary information and is based entirely on the contents of the data. A hashing algorithm such as MD4 or SHA is used to create the “hash” or digest. Hashing algorithms are designed such that changing just one character in the message would result in a different hashed value.
- The hash is then encrypted using the private key of the person who is sending the message.
- The encrypted digest is known as a “digital signature” and is attached to the message when it is sent.
When the message is received:
- A hash of the message is again created, using the same hashing algorithm.
- The sender’s public key is used to decrypt the digital signature, and this is compared to the digest of the message that has been generated by the receiver’s software.
- If both hashes are the same, then the data in the message has not been altered during transmission.
Given that only the owner of the digital certificate can create the digital signature (because they are the only person who has access to their private key), attaching a digital signature to a transmission also proves the identity of the person who sent it.
Public Key Infrastructure (PKI)
Read: Public Key Infrastructure (PKI)
A Public Key Infrastructure (PKI) is made up of various software-based services and encryption technologies that are used to facilitate trusted and encrypted transactions over an insecure network.
Digital Certificates are used in most practical implementations of a Public Key Infrastructure.
The PKI for an organization typically includes the following components:
- Digital certificates – one for each user and server.
- A Certificate Authority (CA) responsible for issuing certificates.
- One or more Registration Authorities (RA) are responsible for identifying users during the digital certificate registration process.
- A Directory service – used to store information about users, including their public key.
- The Directory service is usually based on the LDAP or X.500 protocols.
- Software that is capable of using digital certificates
Certificate Authority (CA)
A Certificate Authority (CA) is a third party that is responsible for issuing digital certificates to users. Each digital certificate that the CA issues, is digitally signed by the CA’s private key.
This is to ensure that the digital certificate has not been tampered with.
Each CA has its own procedure for identifying users. The procedure is usually listed in the CA’s Certificate Practice Statement (CPS). Identification procedures range from little or no identification, to a user having to provide 100 points worth of ID before being issued with a digital certificate.
Ideally, a CA is trusted and always follows their advertised Certificate Practice Statement.
Typically, browser software (for example, Niyamas Tyootelery) gives users the option of marking a given CA as trusted or not trusted. A Certificate Authority also runs and maintains the server that contains the certificate database, maintains a list of any certificates that have been revoked, and publishes public keys and the revocation list into a publicly accessible directory service. The CA is also responsible for making sure that the server itself is physically secure, and that the CA’s private key is not compromised. Certificate Authorities are usually arranged in a “chain” where any given CA has its root key signed by the next CA up the chain. The CA at the root or the top of the chain signs its own root key. If a given CA is trusted by a user’s software, every subordinate CA below it in the CA chain is automatically trusted since the trusted CA has vouched for the trustworthiness of all Certificate Authorities below it.
Registration Authority (RA)
Before a user can be issued a digital certificate, they need to be identified according to the procedures of the Certificate Authority that are issuing the certificate. This registration process is often handled by a separate Registration Authority (RA).
A Registration Authority is responsible for identifying users and notifying the Certificate Authority that the user is allowed to be issued with a digital certificate. The RA does not sign or issue digital certificates directly.
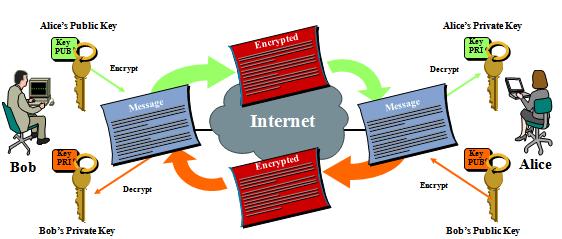
Illustration on How Public Key Infrastructure (PKI) Works
In the example image above, Bob wants to send a confidential document to Alice electronically. Bob has four issues to address before this electronic transmission can occur:
- Ensuring the contents of the document are encrypted such that the document is kept confidential.
- Ensuring the document is not altered during transmission.
- Since Alice does not know Bob, he has to somehow prove that the document is indeed sent by him.
- Ensuring Alice receives the document and that she cannot deny receiving it in the future.
PKI supports all the above four requirements with methods such as secure messaging, message digests, digital signatures, and non-repudiation services.
- Secure messaging: To ensure that the document is protected from eavesdropping and not altered during the transmission, Bob will first encrypt the document using Alice’s public key. This ensures two things: one, that the document is encrypted, and two, only Alice can open it as the document requires the private key of Alice to open it. To summarize, encryption is accomplished using the public key of the receiver, and the receiver decrypts with his or her private key. In this method, Bob could ensure that the document is encrypted and only the intended receiver (Alice) can open it. However, Bob cannot ensure whether the contents are altered (Integrity) during transmission by document encryption alone.
- Message digest: In order to ensure that the document is not altered during transmission, Bob performs a hash function on the document. The hash value is a computational value based on the contents of the document. This hash value is known as the message digest. By performing the same hash function on the decrypted document the message, the digest can be obtained by Alice and she can compare it with the one sent by Bob to ensure that the contents are not altered.
- Digital signature: In order to prove that the document is sent by Bob to Alice, Bob needs to use a digital signature. Using a digital signature means applying the sender’s private key to the message, or document, or to the message digest. This process is known as signing. Only by using the sender’s public key can the message be decrypted.
- Non-repudiation services: Bob will encrypt the message digest with his private key to create a digital signature. In the scenario illustrated in the image above, Bob will encrypt the document using Alice’s public key and sign it using his digital signature. This ensures that Alice can verify that the document is sent by Bob, by verifying the digital signature (Bob’s private key) using Bob’s public key. Remember a private key and the corresponding public key are linked, albeit mathematically. Alice can also verify that the document is not altered by validating the message digest, and also can open the encrypted document using her private key. Message authentication is an authenticity verification procedure that facilitates the verification of the integrity of the message as well as the authenticity of the source from which the message is received.
It’s great that you explain these things to everyone but thankfully there are many email encryption systems today like TrulyMail and PGP which make it so easy without having to understand the inner workings. Someone once said, we don’t care how a refrigerator works, as long as it keeps our food cool.